Harnessing IP Data Streams: Detecting Malicious Intent Patterns


See the exact people visiting your website and Follow up with them.

In today's digital landscape, understanding user behavior is crucial for businesses, especially when it comes to identifying potential threats. IP data streams play a pivotal role in this process, allowing organizations to detect malicious intent patterns effectively.

The Importance of Detecting Malicious Intent
Every year, businesses lose billions due to cyber threats. In fact, the average cost of a data breach is around $4.24 million. By leveraging IP data streams, companies can proactively identify and mitigate these threats before they escalate.
How to Leverage IP Data Streams
To effectively harness IP data streams, follow these actionable steps:
- Identify: Use intent data to pinpoint suspicious IP addresses accessing your website.
- Analyze: Examine the behavior of these IP addresses to determine if they exhibit patterns typical of malicious activity.
- Engage: Implement engagement strategies to either deter or redirect these malicious users.
Common Malicious Intent Patterns
Recognizing the signs of malicious intent can save your business from potential threats. Common patterns include:
- Repeated access attempts from the same IP address.
- Unusual time of access, such as late-night visits.
- Accessing sensitive areas of your website without proper authorization.
Real-World Examples of Malicious Intent Detection
Consider a recent case where a small e-commerce company detected unusual traffic patterns from a specific IP address. By analyzing the data, they found that the IP was attempting to access customer records. Thanks to their proactive monitoring, they were able to block the IP before any data was compromised.
Best Practices for Monitoring IP Data Streams
To ensure effective monitoring of your IP data streams, implement the following best practices:
- Regularly update your security protocols to adapt to new threats.
- Use automated tools to monitor IP data streams in real-time.
- Educate your team on recognizing and responding to potential threats.
Integrating Happierleads for Enhanced Security
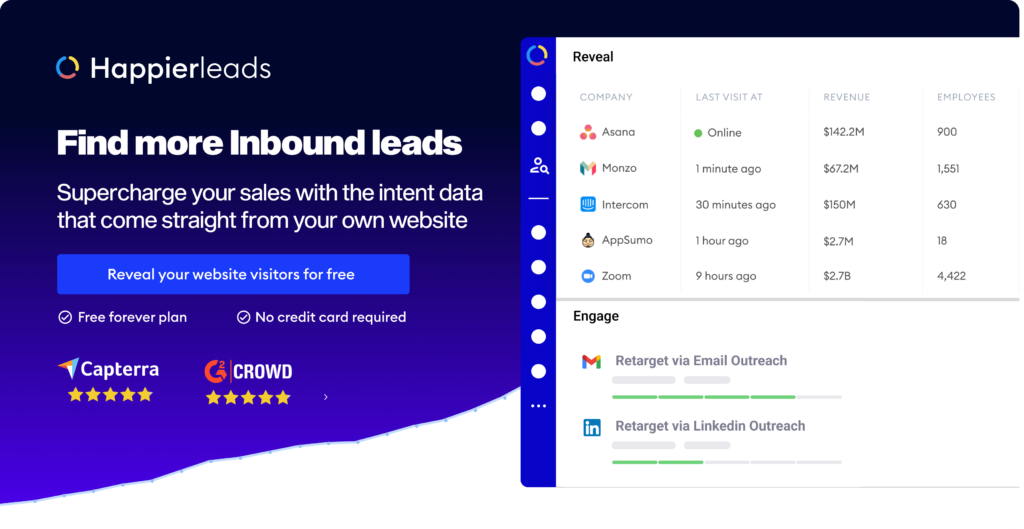
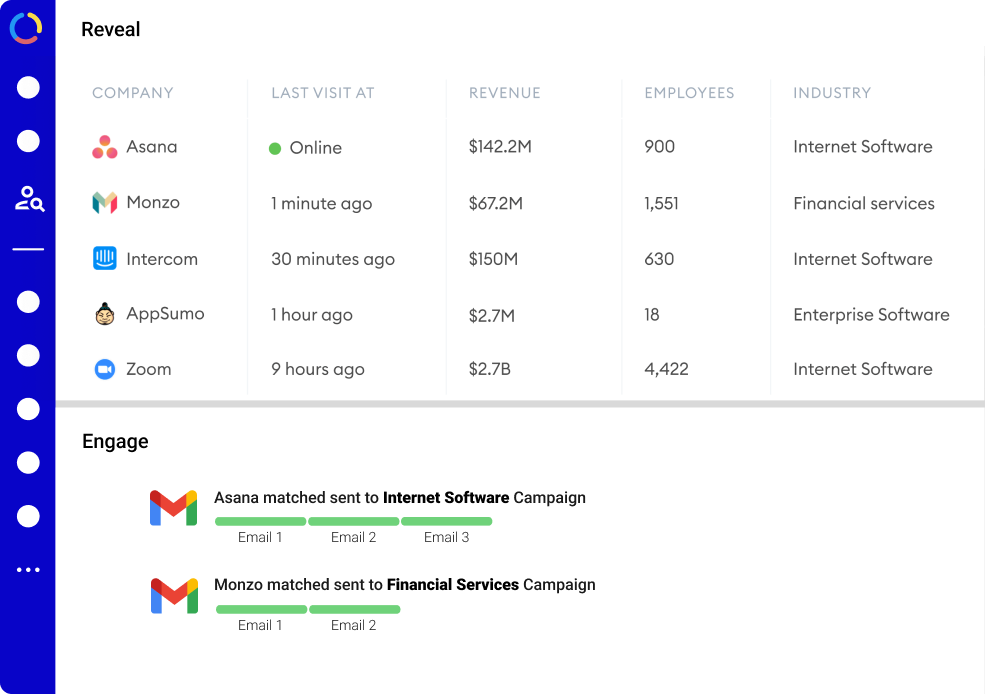
By integrating Happierleads, you can take your threat detection to the next level. Our platform not only identifies anonymous visitors but also qualifies them, making it easier to detect malicious intent and engage effectively.
In today's digital landscape, understanding how to effectively analyze IP data streams is crucial for identifying potential threats. When we talk about IP data streams, we're referring to the flow of information that comes from devices connected to the internet. By examining this data, businesses can uncover patterns that may indicate malicious intent. For instance, if a particular IP address is making an unusually high number of requests to a website, it could signal a potential attack or unauthorized access attempt. This is where the importance of monitoring and analyzing these streams comes into play.
Real-World Applications of IP Data Analysis
Consider a scenario where an e-commerce website experiences a sudden spike in traffic from a specific region. By analyzing the IP data, the security team might discover that a significant portion of this traffic is coming from a single IP address that has a history of malicious activity. In response, they can implement measures to block that IP, protecting their site from potential data breaches or service disruptions. This proactive approach not only safeguards sensitive customer information but also helps maintain the integrity of the business's online presence.
The Role of Behavioral Patterns in Detection
Another important aspect of detecting malicious intent through IP data streams is recognizing behavioral patterns. For example, if a user typically accesses a website during business hours but suddenly starts making requests at odd hours, this could raise a red flag. By establishing a baseline of normal behavior for users, companies can quickly identify deviations that may indicate malicious actions. This kind of analysis can be particularly beneficial for financial institutions, where even a small anomaly can lead to significant consequences. By leveraging these insights, organizations can respond swiftly to potential threats and mitigate risks effectively.
Conclusion
In conclusion, harnessing IP data streams to detect malicious intent patterns is not just a technical necessity; it's a fundamental aspect of maintaining security in an increasingly complex digital environment. By understanding the nuances of IP data and recognizing behavioral patterns, businesses can protect themselves against potential threats. This is where Happierleads comes into play. Our platform helps you identify, qualify, and engage with anonymous website visitors, ensuring that you can turn existing web traffic into valuable leads while enhancing your security measures. Sign up for a free account today and take the first step towards a more secure online presence.
You might also like
Website Identification FAQs
Does Happierleads have a Free trial?
What is Happierleads?
HappierLeads is the only solution that enables you to identify, qualify, and engage with your anonymous B2B website visitors—all within a single tool. No additional licenses or integrations with other outreach automation tools are necessary.
Who typically uses Happierleads?
Happierleads is used by Sales, Growth, and Marketing teams across various industries. If you are a B2B company, we are the solution for you. Sales teams use the platform to turn anonymous traffic into opportunities and increase productivity. While on the other hand, Marketers use the platform to automate lead generation, increase conversions.
How is this different from Clearbit, 6Sense, or DemandBase’s Website Identity Solutions?
Most companies rely on ‘Reverse IP Lookup’ technology to connect IP addresses with company names. At Happierleads, we use a completely different approach—our fully-permissioned, proprietary publisher network—allowing us to identify the exact individuals visiting your website. Discover more about how we identify your site visitors here.
Why is Happierleads ranked number #1 for data quality on G2 and Capterra?
Happierleads offers an advanced feature that automatically filters out bots, ISPs, and other non-qualifying traffic sources to ensure you receive only high-quality leads. Additionally, unlike other tools, Happierleads provides the flexibility for you to manually remove leads as needed.